Remember when SLSA, the software supply chain security framework, dropped in 2021? It was a major win for securing our software pipelines, and integration with Cloud Build has only made things sweeter. If you haven’t checked out the State of the DevOps Report 2022 yet, it’s your guide to why SLSA is worth its weight in coffee beans.
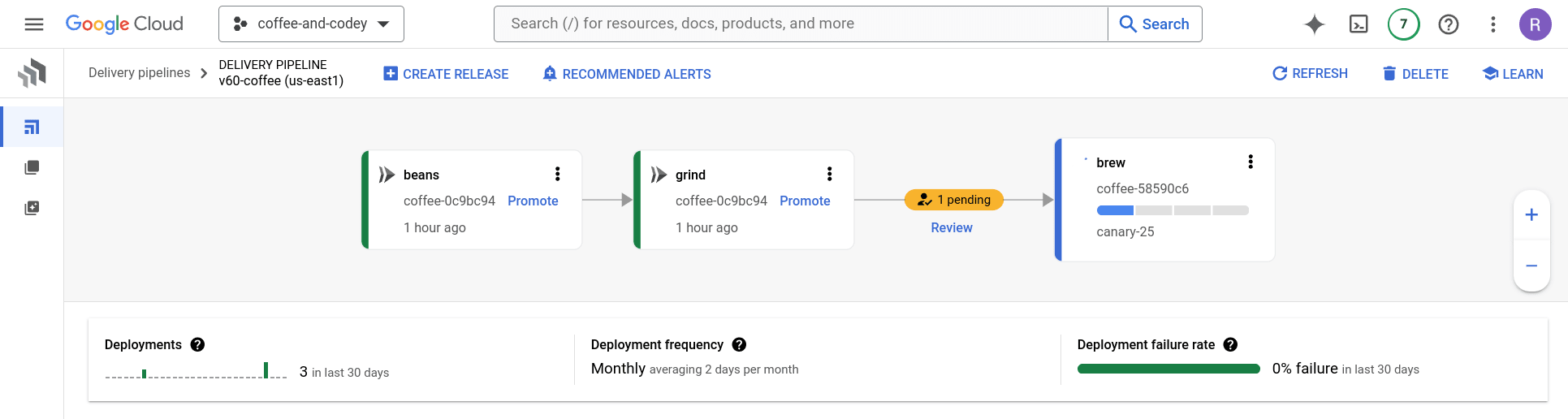
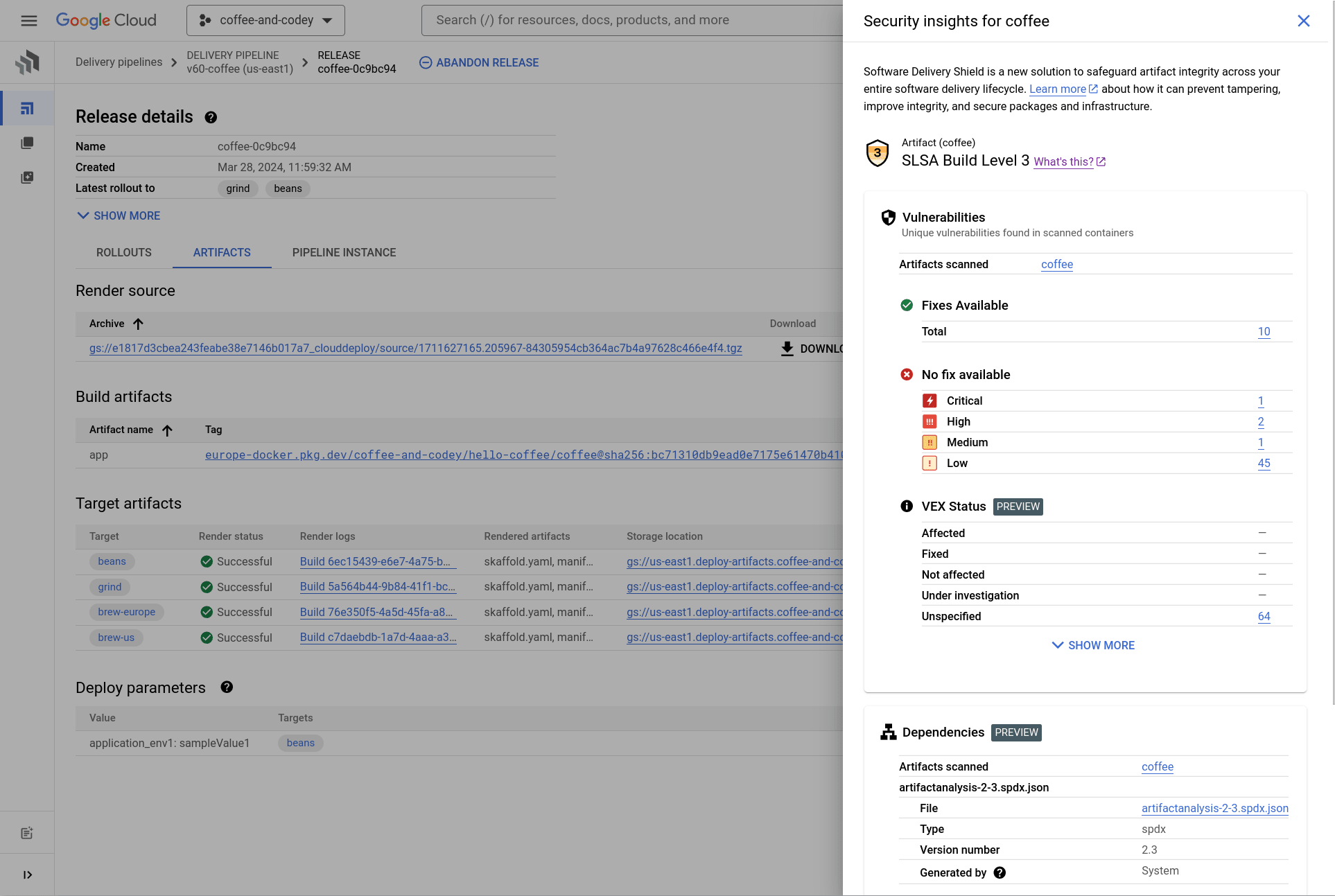
Imagine this: You’re sipping your morning brew, watching a release candidate glide through Cloud Deploy, and boom the CISO ping’s you! Right there, you have a full dashboard of SLSA security information that will help answer and reassure their concerns – vulnerabilities, dependencies, the whole SBOM rundown. It’s like having instant visibility into your deployment’s security posture.
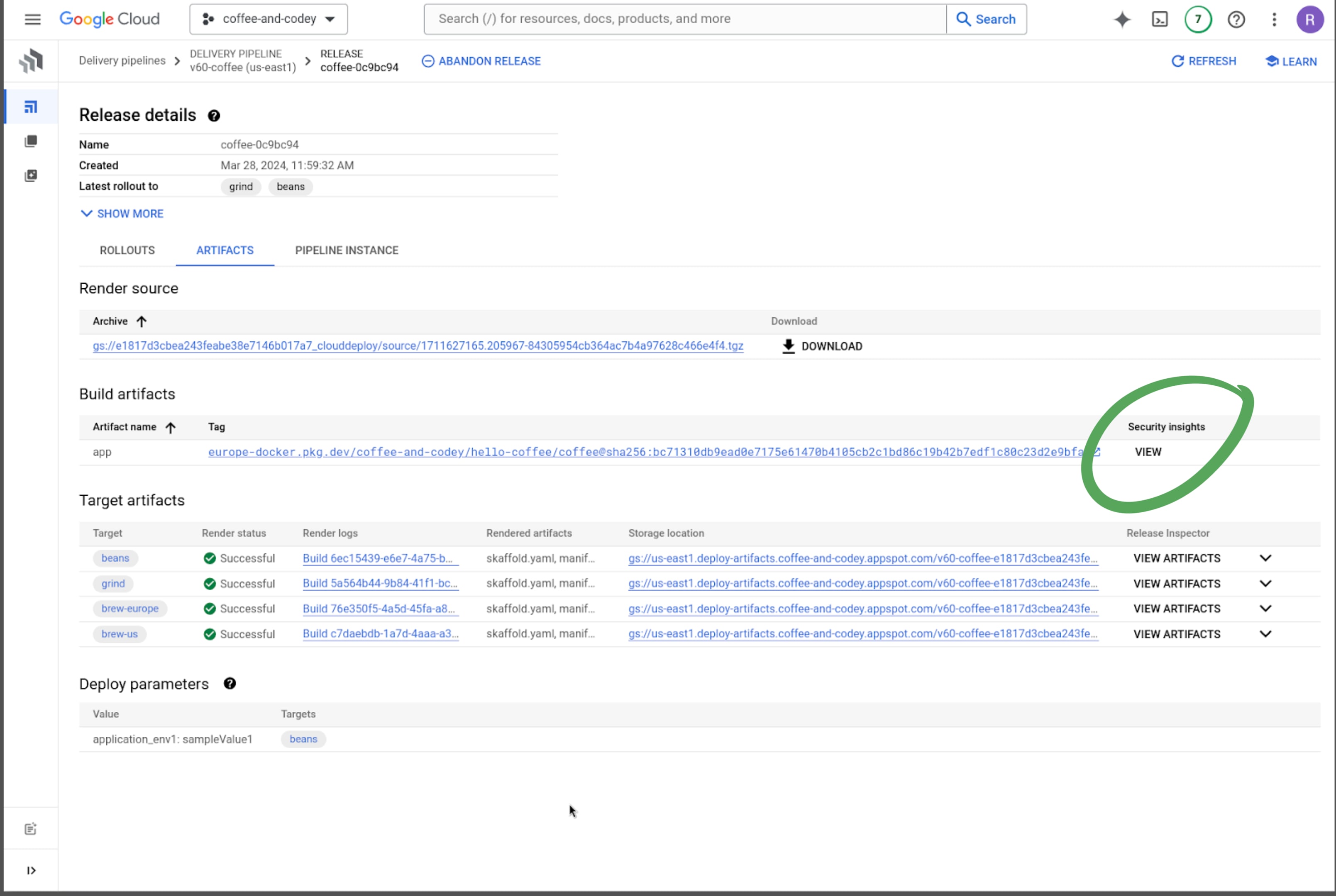
Hold your mugs, let me show you how I navigate to the details: You just browse to your release pipeline, check the artifact details, and click on security insights (you can also go deeper by clicking the relevant hyperlinks).
To get this in your daily routine, you need to give Cloud Deploy the SHA of your release candidate image. Here’s the command-line magic:
gcloud deploy releases create release-candidate-7639a26 --region us-east1 --delivery-pipeline v60-coffee --images app=europe-docker.pkg.dev/<project_id>/<registry>/coffee@sha256:bc71310db9ead0e7175e61470b4105cb2c1bd86c19b42b7edf1c80c23d2e9bfa
The Missing Piece: Automating Release Information
Manually typing that SHA opens us up to the risk of errors, my sausage fingers commonly make mistakes, and it should be automated anyway. Let’s bring in Cloud Build to streamline this. We’ll add some tasks to our build workflow to fetch the image’s SHA and automatically create a Cloud Deploy release candidate. Check out the updated snippet:
# … <your usual Cloud Build setup> …
# Get Image SHA from Artifact Registry
- name: "gcr.io/google.com/cloudsdktool/cloud-sdk"
id: "Get Image Digest"
entrypoint: /bin/bash
args:
- -c
- |
gcloud artifacts docker images describe \
$_AR_HOSTNAME/$PROJECT_ID/$_SERVICE_NAME/$_IMAGE:$COMMIT_SHA \
--format 'value(image_summary.digest)' > /workspace/image-sha.txt
# Generate SBOM (Like having a superpowers inventory!)
- name: gcr.io/google.com/cloudsdktool/cloud-sdk
id: Create a Software Bill of Materials (SBOM)
allowFailure: true
entrypoint: /bin/bash
args:
- -c
- |
gcloud artifacts sbom export --uri ${_AR_HOSTNAME}/${PROJECT_ID}/${_SERVICE_NAME}/${_IMAGE}@$(cat /workspace/image-sha.txt)
# Create a Cloud Deploy Candidate - Unleash the deployment!
- name: gcr.io/google.com/cloudsdktool/cloud-sdk
id: Create a Cloud Deploy Candidate
entrypoint: /bin/bash
args:
- -c
- |
gcloud deploy releases create coffee-${SHORT_SHA} --region ${_DEPLOY_REGION} --delivery-pipeline ${_DEPLOY_PIPELINE} \
--annotations commitID=${REVISION_ID} \
--images app=${_AR_HOSTNAME}/${PROJECT_ID}/${_SERVICE_NAME}/${_IMAGE}@$(cat /workspace/image-sha.txt
(Extracted from https://github.com/sapientcoffee/hello-coffee/blob/main/cloudbuild-deploy.yaml)
Now, your coffee breaks will be even more relaxing (you might even get more with this automation), knowing your software supply chain has a strong dose of built-in security analysis. ☕️
Let me know if you’d like a deeper dive into any part of this! And hey, what other cool things have you brewed up with SLSA, Cloud Build and Cloud Deploy?